Getting started with Fluidkeys in your team
Fluidkeys is a command line application that gives your team PGP encryption superpowers. It makes it simple to share and store sensitive data, safeguard your source code and use popular open source PGP tools.
Fluidkeys automates key rotation and exchange amongst a team. This guide will get you setup as a team and each member of the team setup with new PGP keys.
If you’re already using GnuPG with your team, and want to use these existing keys with Fluidkeys, check out How to import your existing keys GnuPG keys into Fluidkeys
Contents:
- Prerequisites: Install Fluidkeys
- Setup your team in Fluidkeys
- Invite people to join
- Authorize people’s requests to join
- Keep the teams’ keys in sync
Prerequisites: Install Fluidkeys
Set up your team
The fk team create command gets you started in creating a team in Fluidkeys. The first thing you’ll be asked is what’s your team email address?
fk team create What's your team email address? This is how other people using Fluidkeys will find you. We'll send you an email to verify your address. [email] :
After providing your email address, Fluidkeys will present you with a strong six word password password. It’s save this in your system’s keyring so you don’t have to keep typing it and so that Fluidkeys can automate tasks like rotating your key each month.
It’s important to save a backup of this password. We recommend putting it into a password manager as a backup.
Store your password We've made you a strong password to protect your secrets: 🤫 mushroom.departure.backpack.dwelled.circling.figurine The password will be saved to your macOS Keychain so you don't have to keep typing it. You should save a copy in your own password manager as a backup. Press enter when you've saved the password.
Behind the scenes, Fluidkeys will generate you a PGP key and store this in GnuPG. The email address you provide will be associated with this key, and the password Fluidkeys provides will be used to protect this key. You can see this key in GnuPG by running gpg --list-secret-keys
Next Fluidkeys will check you’ve stored your password by wiping the screen and prompting you to repeat back one of the words. You’ll then be prompted to verify your email address.
Fluidkeys will then complete a number of tasks to create your key, before asking you for your team name:
What's your team name?
This is how your team will be displayed to you and other members. You can
always change this later.
[team name] :
Fluidkeys will then create a roster for the team which is a list of all the people in it. At this point, this will just be you. You’ll get a chance to preview it, before being prompted to sign it and upload it to our team server.
Cryptographically signing the roster means your other team members can validate that you, and only you, have edited this file.
Everyone in the team has a copy of this roster and it is used to lookup which key to use for an email address and fetch the corresponding keys.
Creating signed team roster
Create team roster with you in it:
── Preview of roster.toml ──────────────────────────────────────────────────
# Kiffix team roster. Everyone in the team has a copy of this file.
#
# It is used to look up which key to use for an email address and fetch keys
# automatically.
uuid = "e4959b34-ef41-4e2a-b3bd-fb2604c62c0e"
name = "Kiffix"
[[person]]
email = "jane@kiffix.com"
fingerprint = "4C83FCD3D404EBC41BE298C6129054800CDE2D77"
is_admin = true
────────────────────────────────────────────────────────────────────────
Sign and upload the roster to Fluidkeys now? [y/n]
Invite people to join your team
Once signed and uploaded, you’ll then be given an invitation you can share with your team members to join you:
── Invitation to join Kiffix ───────────────────────────────────────────────────
Join Kiffix on Fluidkeys
I've created a team on Fluidkeys to make it simple for us to share passwords
and secrets securely.
Join now:
1. download Fluidkeys from https://download.fluidkeys.com
2. apply to join the team by running:
> fk team apply e4959b34-ef41-4e2a-b3bd-fb2604c62c0e
3. reply to me with your verification details so I can authorize you
────────────────────────────────────────────────────────────────────────────────
When each of your team members runs fk team apply ... they’ll be guided through a similar set-up you did when creating the team: they’ll be asked what email address they want to use, be given a strong password. Finally they’ll be given a message to relay back to you to authorise their request to join the team.
It’ll look like this:
── Please authorize me to join Kiffix ──────────────────────────────────────────
I've requested to join Kiffix on Fluidkeys.
Here are my verification details:
» key: F357 9950 9697 694A 66E0 A26D 953C B86F F357 B12D
email: tina@example.com
Please can you authorize me by running
> fk team authorize
────────────────────────────────────────────────────────────────────────────────
Resending invitations
If you lose this invitation at a future date, you can always get the invitation code by running fk status
│ ℹ️ Invite others to join Kiffix
│
│ Your team members can request to join the team by running
│ fk team apply e4959b34-ef41-4e2a-b3bd-fb2604c62c0e
Authorizing requests
Authorizing requests
Once various members of your team have applied to join your team, you’ll need to authorize them. You can do this with the fk team authorize command.
fk team authorize 1 request to join Kiffix: 1. tina@example.com » key: F357 9950 9697 694A 66E0 A26D 953C B86F F357 B12D email: tina@example.com Authorize tina@example.com now? (type n to decide later) [y/n]
It’s important to check that the key and email information you’re presented running this command for each request matches what your team member sent you:
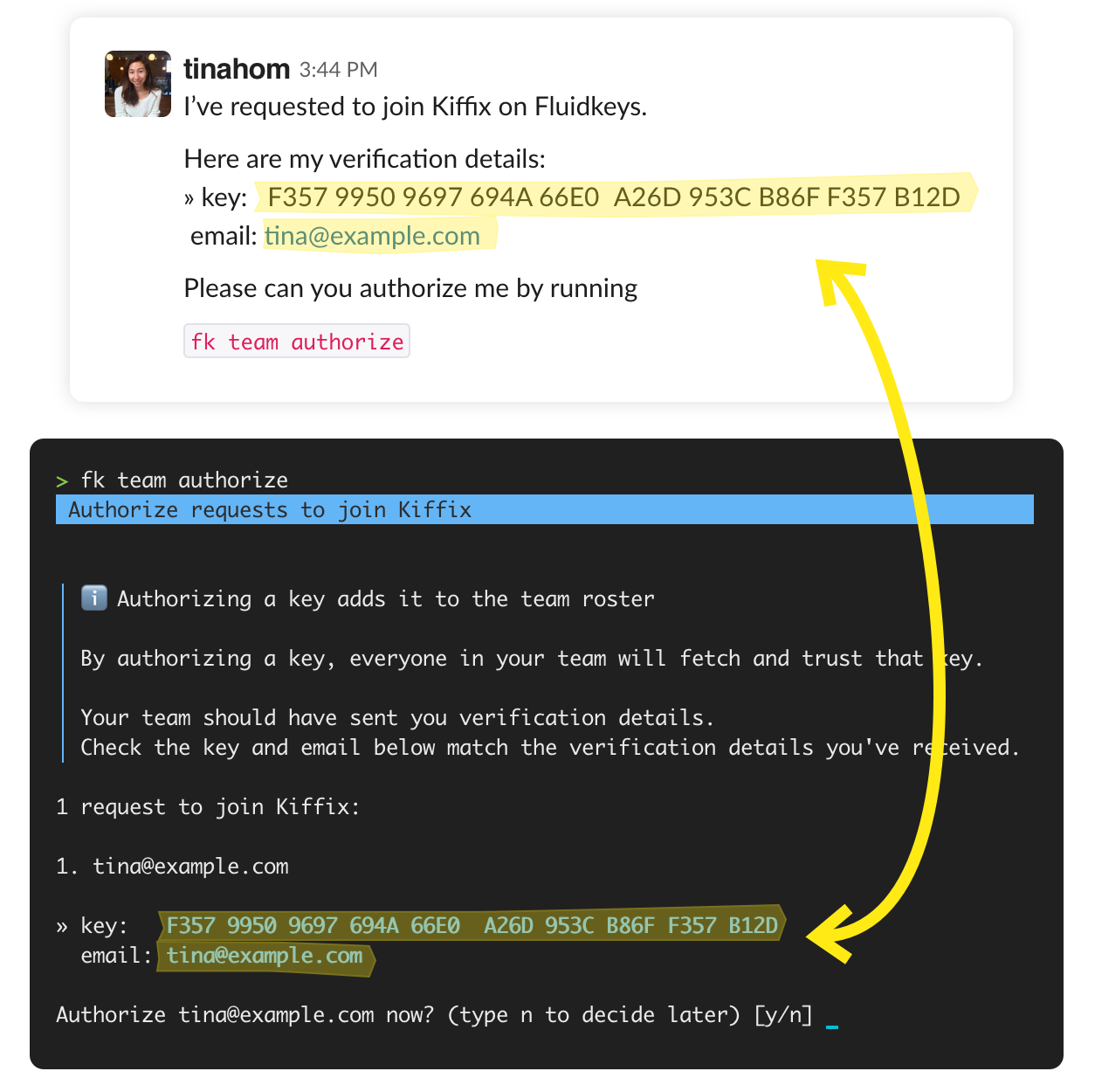
This is to ensure it really is them requesting to join the team, and not someone else trying to gain access!
You can always postpone making a decision on whether to authorize someone or not, by typing n. You can also reject requests, which means the team member would have to apply again to gain access.
Once you’ve finished authorising the requests, you’ll be prompted to sign and upload an updated roster.
Keep your keys in sync
Once this team roster is uploaded to Fluidkeys you and your team members can run fk team fetch to download one another’s keys and import them into GnuPG.
By default, Fluidkeys does this for you each day in the background. That way you’ll know you always have the latest key for each person and that they rotate each month.